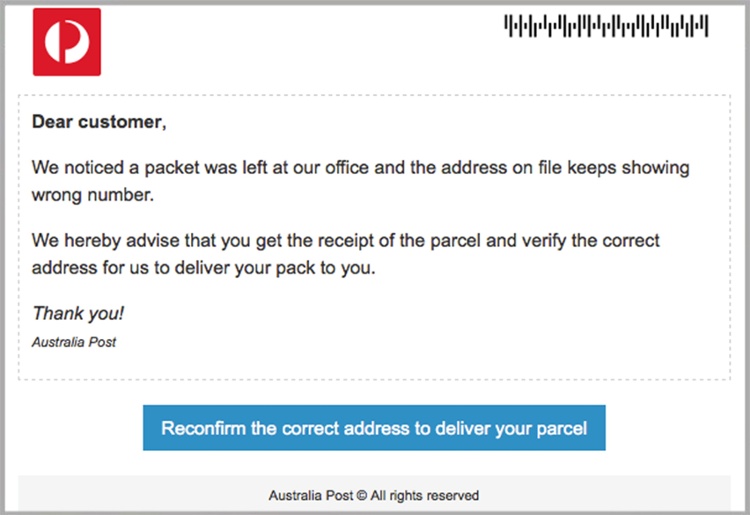
A massive run of scam Australia Post emails is bombarding inboxes with malware, with a clever ploy designed to evade virus-detection software.
The email started distribution this morning, hitting thousands of inboxes within an hour. The message tells recipients they have a parcel to be collected at the post office. It uses Australia Post branding – and awkward grammar – to ask recipients to confirm their correct postal address by clicking a link.
However, those who click the link invite malware onto their system by downloading a remotely-executed malicious file.
The criminals behind the scam try to outrun traditional, reactive antivirus technology by sending out multiple versions of the email, with small changes to the wording such as the subject line or body content. This practice is known as content spinning (see explanation below).
While our filter intercepted and blocked the email to its global client base, only one of 68 popular antivirus vendors were detecting the link as malicious.
Those who follow the prompts are led to a highly-sophisticated replica of the real Australia Post website, complete with a ‘Captcha’ security form to help imply legitimacy. The scammers registered the domain www.auspost.tk to host the fake website. The ‘.tk’ suffix stands for Tokelau, a tiny group of atolls located between New Zealand and Hawaii known as a frequent originator of phishing emails.
What is content spinning?
Curious to know why email scam attempts are often let down by awkward wording and poor grammar? While sometimes it’s because the cybercriminals are based overseas, and English isn’t their first language, there’s another good explanation: it helps their success rate.
Traditional antivirus detection technology is signature-based.
Signature-based detection systems examine the text in an email, and mathematically derive a unique identifier based on that text. This identifier is used to categorise emails; it might raise a red flag that that particular block of text is known to be used in scam emails.
However, if so much as a letter changes from one email to the next, that unique identifier is immediately superseded. As such, the old signature will not work and the threat will not be detected.
Advice on email scams from Australia Post
Australia Post’s website offers advice on spotting a scam. It says Australia Post never:
- Emails you to reconfirm your physical mailing address by clicking on a link
- Asks you to click on an email link to print off a label to redeem your package
- Emails or calls you to ask for personal or financial information including password, credit card details or account information
- Calls or emails out of the blue to request payment.
Australia Post asks people to report suspected scams to SCAMwatch or Stay Smart Online. You can also report any suspicious Australia Post-branded emails to scams@auspost.com.au.